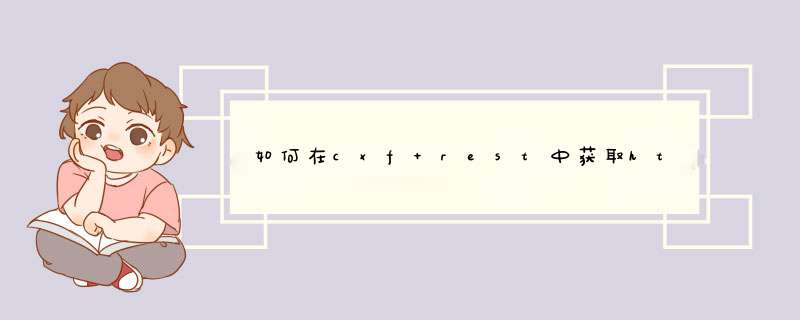
1)使用@HeaderParam
Java代码
1.BaseRespObj postHello(@HeaderParam("User-Agent")final String userAgent, @FormParam("id")final int id)
BaseRespObj postHello(@HeaderParam("User-Agent")final String userAgent, @FormParam("id")final int id)
2)使用@Context
Java代码
1.public class HelloServiceImpl implements IHelloService {
2.@Context
3.protected HttpServletRequest req
4.
5.public Hello getHello(int id) {
6.System.out.println(req.getHeader("User-Agent"))
7.
8.}
9.}
public class HelloServiceImpl implements IHelloService {
@Context
protected HttpServletRequest req
public Hello getHello(int id) {
System.out.println(req.getHeader("User-Agent"))
}
}
第二种方式不需要在每个接口中都把header作为参数传入,使接口更为简洁。可封装BaseRest统一处理header即可。
CXF本身应该有更方便的方式进行添加,去读读文档。我当时也遇到这个问题,时间太紧我没时间读文档,用了一个很笨很直接的办法:
我当时的场景:对方服务是用.net开发的,我用JAVA&CXF,他自己用.net很顺序地能调通,我用CXF就不行。
我的笨办法:
1、我搞到别人能调通的SOAP报文;
2、抓到我CXF调用发出的报文;
3、比较两者之不同;
4、然后自己在拦截器中把差的报文节点补齐;
5、搞定。(看起来复杂,其实没花多少时间)
代码虽然还一翻就找到了,附上希望给你一点思路。
public class HeaderIntercepter extends AbstractPhaseInterceptor<SoapMessage>{
public static final String xml_namespaceUR_att = "http://tempuri.org/"
public static final String xml_head_el = "RoadSoapHeader"
public static final String xml_userID_el = "UserID"
public static final String xml_password_el = "PassWord"
public static final String userId = ""
public static final String password= ""
public RoadHeaderIntercepter() {
super(Phase.WRITE)
}
/**
* @param message
* @throws Fault
* @see org.apache.cxf.interceptor.Interceptor#handleMessage(org.apache.cxf.message.Message)
*/
@Override
public void handleMessage(SoapMessage message) throws Fault {
QName qname = new QName(xml_head_el)
Document doc = DOMUtils.createDocument()
Element userIdElement = doc.createElement(xml_userID_el)
userIdElement.setTextContent(userId)
Element passwordElement = doc.createElement(xml_password_el)
passwordElement.setTextContent(password)
Element root = doc.createElementNS(xml_namespaceUR_att, xml_head_el)
root.appendChild(userIdElement)
root.appendChild(passwordElement)
//XMLUtils.printDOM(root)SoapHeader head = new SoapHeader(qname, root)
List<Header>headers = message.getHeaders()
headers.add(head)
}
}
<jaxws:client id="client"
serviceClass="xxx.RoadAskOutServiceSoap"
address="${address}/RoadAskOutService.asmx">
<jaxws:outInterceptors>
<bean class="xxx.HeaderIntercepter"></bean>
</jaxws:outInterceptors>
</jaxws:client>
UTPP令牌验证是 ws-security 规范中约定的最简单的一种验证方式,以下是5年前我用xfire 的代码,希望能对你有帮助,cxf 也是从 xfire 发展来的,估计语法上大同小异
Client client = ((XFireProxy) Proxy.getInvocationHandler(service)).getClient()
client.addOutHandler(new DOMOutHandler())
Properties config = new Properties()
// Action to perform : user token
config.setProperty(WSHandlerConstants.ACTION, WSHandlerConstants.USERNAME_TOKEN)
// Password type : plain text
config.setProperty(WSHandlerConstants.PASSWORD_TYPE, WSConstants.PW_TEXT)
// for hashed password use:
//properties.setProperty(WSHandlerConstants.PASSWORD_TYPE, WSConstants.PW_DIGEST)
// User name to send
config.setProperty(WSHandlerConstants.USER, "serveralias")
// Callback used to retrive password for given user.
config.setProperty(WSHandlerConstants.PW_CALLBACK_CLASS, PasswordHandler.class.getName())
client.addOutHandler(new WSS4JOutHandler(properties))
service.doSomething(...)
-------------------------------------------------------------------------------------------------
public class PasswordHandler implements CallbackHandler {
private Map passwords = new HashMap()
public PasswordHandler() {
passwords.put("serveralias", "aliaspass")
passwords.put("client-344-839","client344Password")
}
public void handle(Callback[] callbacks) throws IOException,
UnsupportedCallbackException {
WSPasswordCallback pc = (WSPasswordCallback) callbacks[0]
String id = pc.getIdentifer()
pc.setPassword((String) passwords.get(id))
}
}
--------------------------------------------
要用到 wss4j 和 bcprov ,如果仅仅是令牌验证的话,可以不用 bcprov,如果做签名和消息级加密的话,就必须要用到 bcprov 或是其他的安全包了
欢迎分享,转载请注明来源:内存溢出

 微信扫一扫
微信扫一扫
 支付宝扫一扫
支付宝扫一扫
评论列表(0条)