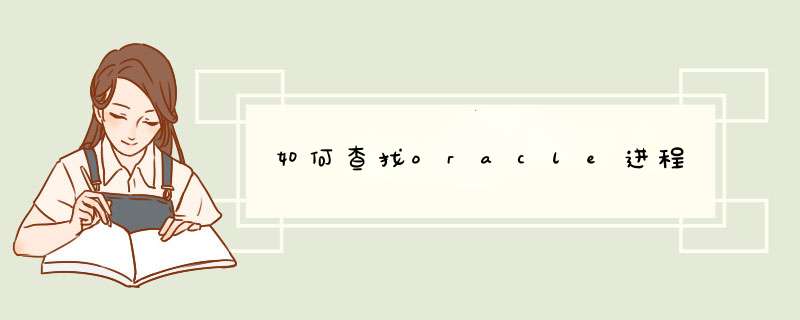
SELECT b.sql_text, sid, serial#, osuser, machine
FROM v$session a, v$sqlarea b
WHERE a.sql_address = b.address
查询前台发出的SQL语句.
select user_name,sql_text
from v$open_cursor
where sid in
(select sid from (select sid,serial#,username,program from v$session where status='ACTIVE'))
根据SPID查询session
SELECT * FROM v$session WHERE paddr IN
(SELECT addr FROM v$process WHERE spid=&spid)
根据SID查询process
SELECT * FROM v$process WHERE addr IN
(SELECT paddr FROM v$session WHERE sid=&sid)
DBA如何查询其他用户所进行的 *** 作
SELECT sql_text
FROM v$sql t1, v$session t2
WHERE t1.address = t2.sql_address
AND t2.sid = &sid
根据process查询sql语句
SELECT sql_text
FROM v$sqltext a
WHERE (a.hash_value, a.address) IN (
SELECT DECODE (sql_hash_value,0, prev_hash_value,sql_hash_value ),
DECODE (sql_hash_value, 0, prev_sql_addr, sql_address)
FROM v$session b
WHERE b.paddr = (SELECT addr
FROM v$process c
WHERE c.spid = '$processID'))
ORDER BY piece ASC
其他
执行下列命令语句
sqlplus / as sysdba <<EOF
create tablespace test datafile '/data/test01.dbf' size 10240M
quit
EOF
通过ps -ef|grep sqlplus命令得到上面所执行的命令的进程id为:12345
(1)关于v$process
执行下面的SQL是查不到相关的信息:
select * from v$process where spid='12345';
因为这个spid字段对应的并不是我们用ps命令从系统中查询到的进程id,而是这个进程执行的当前SQL的进程id,
也就是上面命令中的“create tablespace test datafile '/data/test01.dbf' size 10240M”所对应的进程id,如果想
通过用ps命令从系统中查询到的进程id查看对应的信息,那么必须使用下面语句:
select spid,sid,process,sql_address from v$session where process='12345'
上面sql中的process就是通过ps查看的进程id,而spid就是里面的sql语句所对应的进程id。
还可以通过上面的sql_address 查看正在执行的SQL语句内容:
select sql_text from v$sqlarea s,v$session ses where s.address=ses.sql_address and ses.process='12345'
(2)关于v$session
在查询 v$session 视图的时候,我们根据command字段内部表示解码每一个字段,当我们需要快速找出他们的 Oracle 系统的内部情况时非常有用。
select
substr(s.username,1,18) username,substr(s.program,1,15) program,p.spid,s.process,
decode(s.command,
0,'No Command',
1,'Create Table',
2,'Insert',
3,'Select',
6,'Update',
7,'Delete',
9,'Create Index',
15,'Alter Table',
21,'Create View',
23,'Validate Index',
35,'Alter Database',
39,'Create Tablespace',
41,'Drop Tablespace',
40,'Alter Tablespace',
53,'Drop User',
62,'Analyze Table',
63,'Analyze Index',
s.command||': Other') command
from
v$session s,
v$process p,
v$transaction t,
v$rollstat r,
v$rollname n
where s.paddr = p.addr
and s.taddr = t.addr (+)
and t.xidusn = r.usn (+)
and r.usn = n.usn (+)
order by username
(3)几个相关的SQL
--查看系统进程对应的信息
select se.saddr,se.sid,se.serial#,p.pid,se.paddr,s.sql_id,s.sql_text
from v$session se ,v$process p, v$sqlarea s
where se.paddr=p.addr and se.sql_address=s.address and se.process='&1'
and se.username is not null
--查看所有的会话
select se.username,se.saddr,se.sid,se.serial#,se.process,s.sql_id
from v$session se,v$sqlarea s
where se.sql_address=s.address
--查看会话对应的sql内容
select se.username,se.process,s.sql_text
from v$session se,v$sqlarea s
where se.sql_address=s.address and s.sql_id='&1'
查看ORACLE最大进程数:SQL>select count(*) from v$session #连接数
SQL>Select count(*) from v$session where status='ACTIVE' #并发连接数
SQL>show parameter processes #最大连接
SQL>alter system set processes = value scope = spfile重启数据库 #修改连接
unix 1个用户session 对应一个 *** 作系统 process
而 windows体现在线程
------------------------------------------------------------------------------
修改ORACLE最大进程数:
使用sys,以sysdba权限登录:
SQL>show parameter processes
NAME TYPEVALUE
------------------------------------ ----------- ------------------------------
aq_tm_processes integer 1
db_writer_processes integer 1
job_queue_processes integer 10
log_archive_max_processesinteger 1
processesinteger 150
SQL>alter system set processes=300 scope = spfile
系统已更改。
SQL>show parameter processes
NAME TYPEVALUE
------------------------------------ ----------- ------------------------------
aq_tm_processes integer 1
db_writer_processes integer 1
job_queue_processes integer 10
log_archive_max_processesinteger 1
processesinteger 150
SQL>create pfile from spfile
文件已创建。
重启数据库,
SQL>show parameter processes
NAME TYPEVALUE
------------------------------------ ----------- ------------------------------
aq_tm_processes integer 1
db_writer_processes integer 1
job_queue_processes integer 10
log_archive_max_processesinteger 1
processesinteger 300
欢迎分享,转载请注明来源:内存溢出

 微信扫一扫
微信扫一扫
 支付宝扫一扫
支付宝扫一扫
评论列表(0条)