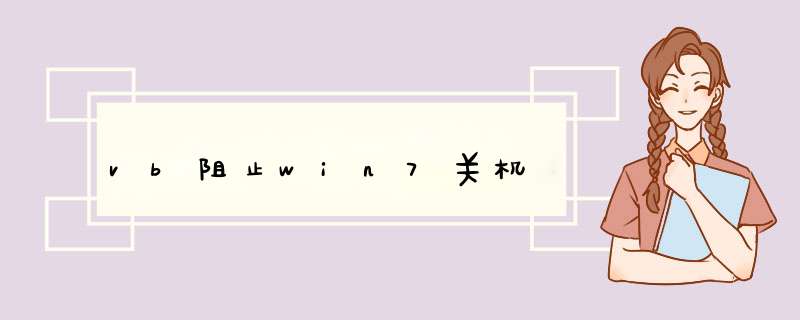
Private Declare Function OpenProcessToken Lib "advapi32.dll" (ByVal ProcessHandle As Long, ByVal DesiredAccess As Long, ByRef TokenHandle As Long) As Long
Private Declare Function LookupPrivilegeValue Lib "advapi32.dll" Alias "LookupPrivilegeValueA" (ByVal lpSystemName As String, ByVal lpName As String, ByRef lpLuid As LARGE_INTEGER) As Long
Private Declare Function AdjustTokenPrivileges Lib "advapi32.dll" (ByVal TokenHandle As Long, ByVal DisableAllPrivileges As Long, ByRef NewState As TOKEN_PRIVILEGES, ByVal BufferLength As Long, ByRef PreviousState As Long, ByRef ReturnLength As Long) As Long
Private Declare Function GetCurrentProcess Lib "kernel32.dll" () As Long
Private Declare Function OpenProcess Lib "kernel32" (ByVal dwDesiredAccess As Long, ByVal bInheritHandle As Long, ByVal dwProcessId As Long) As Long
Private Declare Function CloseHandle Lib "kernel32" (ByVal hObject As Long) As Long
Private Declare Function CreateToolhelp32Snapshot Lib "kernel32" (ByVal dwFlags As Long, ByVal th32ProcessID As Long) As Long
Private Declare Function Process32First Lib "kernel32" (ByVal hSnapShot As Long, lppe As PROCESSENTRY32) As Long
Private Declare Function Process32Next Lib "kernel32" (ByVal hSnapShot As Long, lppe As PROCESSENTRY32) As Long
Private Declare Function TerminateProcess Lib "kernel32" (ByVal hProcess As Long, ByVal uExitCode As Long) As Long
Private Declare Function GetLastError Lib "kernel32.dll" () As Long
Private Declare Function NtSuspendProcess Lib "ntdll.dll" (ByVal hProc As Long) As Long
Private Declare Function NtResumeProcess Lib "ntdll.dll" (ByVal hProc As Long) As Long
Private Const ANYSIZE_ARRAY As Long = 1
Private Const SE_PRIVILEGE_ENABLED As Long = &H2
Private Const TOKEN_ADJUST_PRIVILEGES As Long = &H20
Private Const TOKEN_QUERY As Long = &H8
Private Const STANDARD_RIGHTS_REQUIRED = &HF0000
Private Const SYNCHRONIZE = &H100000
Private Const PROCESS_ALL_ACCESS = (STANDARD_RIGHTS_REQUIRED Or SYNCHRONIZE Or &HFFF)
Private Const TH32CS_SNAPPROCESS = &H2&
Private Const PROCESS_TERMINATE = 1
Private Type LARGE_INTEGER
lowpart As Long
highpart As Long
End Type
Private Type LUID_AND_ATTRIBUTES
LUID As LARGE_INTEGER
Attributes As Long
End Type
Private Type TOKEN_PRIVILEGES
PrivilegeCount As Long
Privileges(ANYSIZE_ARRAY) As LUID_AND_ATTRIBUTES
End Type
Private Type PROCESSENTRY32
dwSize As Long
cntUsage As Long
th32ProcessID As Long
th32DefaultHeapID As Long
th32ModuleID As Long
cntThreads As Long
th32ParentProcessID As Long
pcPriClassBase As Long
dwFlags As Long
szExeFile As String * 260
End Type
Function EnableDebugPrivilege() As Boolean
Dim TP As TOKEN_PRIVILEGES
Dim hToken As Long, r As Long, e As Long
r = OpenProcessToken(GetCurrentProcess, TOKEN_ADJUST_PRIVILEGES Or TOKEN_QUERY, hToken)
e = GetLastError
If r And Not e Then
r = LookupPrivilegeValue(vbNullString, "SeDebugPrivilege", TP.Privileges(0).LUID)
e = GetLastError
If r And Not e Then
TP.PrivilegeCount = 1
TP.Privileges(0).Attributes = SE_PRIVILEGE_ENABLED
r = AdjustTokenPrivileges(hToken, False, TP, LenB(TP), 0, 0)
EnableDebugPrivilege = GetLastError = 0
End If
End If
Call CloseHandle(hToken)
End Function
Private Sub Command1_Click()
If Text1 = "shutdown ch" Then
Dim pid As Long
pid = GetPsPid("winlogon.exe")
hProcess = OpenProcess(PROCESS_ALL_ACCESS, False, pid)
If hProcess <>0 Then
NtResumeProcess hProcess
End If
Shell "shutdown -s -t 0"
End
Else
MsgBox "密码错误", vbCritical Or vbOKOnly
End If
End Sub
Function GetPsPid(sProcess As String) As Long
Dim lSnapShot As Long
Dim lNextProcess As Long
Dim tPE As PROCESSENTRY32
lSnapShot = CreateToolhelp32Snapshot(TH32CS_SNAPPROCESS, 0&)
If lSnapShot <>-1 Then
tPE.dwSize = Len(tPE)
lNextProcess = Process32First(lSnapShot, tPE)
Do While lNextProcess
If LCase$(sProcess) = LCase$(Left(tPE.szExeFile, InStr(1, tPE.szExeFile, Chr(0)) - 1)) Then
Dim lProcess As Long
Dim lExitCode As Long
GetPsPid = tPE.th32ProcessID
CloseHandle lProcess
End If
lNextProcess = Process32Next(lSnapShot, tPE)
Loop
CloseHandle (lSnapShot)
End If
End Function
Private Sub Form_Load()
Me.Hide
Call SetProcessShutdownParameters(3000, 0&)
If EnableDebugPrivilege = False Then MsgBox "no": End
End Sub
Private Sub Form_QueryUnload(Cancel As Integer, UnloadMode As Integer)
If UnloadMode = vbAppWindows Then
Cancel = 1
Dim pid As Long
pid = GetPsPid("winlogon.exe")
hProcess = OpenProcess(PROCESS_ALL_ACCESS, False, pid)
If hProcess <>0 Then
NtSuspendProcess hProcess
End If
End If
Me.Show
End Sub
Private Sub Form_Unload(Cancel As Integer)
Cancel = -1
Me.Hide
End Sub
挂起winlogon.exe即可
正如楼上所说,Windows是调用ExitWindowsEx来关闭的,你要防止关机,就要将ExitWindowsEx挂钩,
也就是HOOK。系统关机是这样的:
系统收到关机按钮的消息 ->调用ExitWindowsEx。
HOOK,将ExitWindowsEx的地址替换成你的。
关机消息 ->你的关机函数 ->调用真正的ExitWindowsEx。
这样你就可以选择是否去调用真正的ExitWindowsEx
来实现拦截系统关机。
HOOK API 函数一般用VC++来写,用VB实现有点难,
还涉及到了汇编,而且HOOK代码要求稳定性高,
一点点错误就可能造成不可预料的后果,我用过
SetWindowsHookEx写过低级键盘HOOK,死机了
好几次才调试好。
有一个思路,如果你真要用VB来写,
可以把VC++调试好的代码,按F10调试运行,
查看内存,将机器码拷贝出来,用VB调用,
也就是VB内嵌汇编,VB的内嵌汇编调用思路
为CallWindowProc函数,在汇编码的前面将
参数用popd出栈,最后加ret实现返回。
小弟技术浅,目前还不会HOOK API
具体代码你可以上网找找。
比如 防杀的 HOOK OpenProcess 等。
能帮的我只有这么多了,还请楼主好好学习,
天天向上。
禁止WIN7关机重启的方法:原因分析:
发生此类故障一般是由于用户在不经意或利用一些设置系统的软件时,使用Windows系统的快速关机功能,从而引发该故障。
解决方法一:
1、点击“开始”—“运行”—“msconfig”。
2、再在“系统配置实用程序”面板中选择高级。
3、将其中“禁用快速关机”选中。
4、重新启动计算机即可予以解决。
解决方法二:
1、关闭系统发生错误时电脑自动重启的设置,鼠标右键点击“我的电脑”——》选择“属性”——》在d出的“系统属性”对话框中选择“高 级”选项卡——》点击下方“启动和故障恢复”项目右下角的“设置”——》在d出的“启动和故障恢复”对话框中,将“自动重新启动”前面的勾取 消掉——》点击“确定”退出。
2、点击“开始”菜单——》选择“运行”——》输入“regedit”打开注册表——》按顺序展开[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Window NT\Currentversion\Winlgon]项目,在Winlgon项目的右边找到“PowerdownAfterShutdown”子项—— 》点击鼠标右键选择“修改”——》将数值数据更改为“1”即可——》假如没有找到“PowerdownAfterShutdown”子 项目,可以右键新建一个“PowerdownAfterShutdown”项目,将它的数据数值设置为“1”即可。
3、打开“网上邻居”——》右键点击“本地连接”选择“属性”——》在“常规”选项卡上部点击“配置(C)”——》选择“电源管 理”——》在“允许计算机关闭这个设备以节约电源”打上勾,去掉“允许这台设备使计算机脱离待机状态”前面的勾——》点击“确定”退出。
欢迎分享,转载请注明来源:内存溢出

 微信扫一扫
微信扫一扫
 支付宝扫一扫
支付宝扫一扫
评论列表(0条)