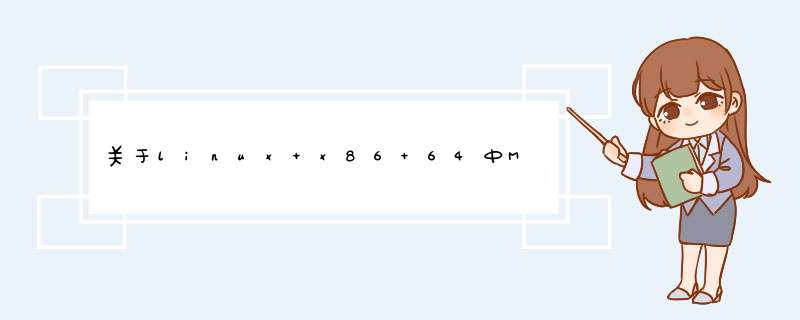
当前的最终汇编代码是:
movq %%gs:0xb000,%0
上面的代码可以工作!但是当我打印%% gs时,它的值为0,所以%% gs指向GDT NulL的第一项!!这个怎么运作?
mov %%gs,%0
相反,gs的基础在MSR_GS_BASE中,并且当前可以替换为:
/*0xb000 is the offset of per_cpu__current_task*/cur_task = (unsigned long*)(x86_rdmsr64(MSR_GS_BASE) + 0xb000);println("cur_task:%p",*cur_task); 我的问题是:
%gs指向GDT NulL的第一项!! ??如何从MSR_GS_BASE读取它是一个cpu功能?我需要一些关于此的参考.
解决方法 从 AMD Architecture Programmer’s Manual Volume 2: System Programming开始,第4.5.3节:总结FS and GS Registers in 64-Bit Mode. Unlike the CS,DS,ES,and SS segments,the FS and GS segment overrIDes can be used in 64-bit mode. When FS and GS segment overrIDes are used in 64-bit mode,their respective base addresses are used in the effective-address (EA) calculation. The complete EA calculation then becomes (FS or GS).base + base + (scale * index) + displacement. The FS.base and GS.base values are also expanded to the full 64-bit virtual-address size,as shown in figure 4-5. The resulting EA calculation is allowed to wrap across positive and negative addresses.
[…]
There are two methods to update the contents of the FS.base and GS.base hIDden descriptor fIElds. The first is available exclusively to privileged software (CPL = 0). The FS.base and GS.base hIDden descriptor-register fIElds are mapped to MSRs. Privileged software can load a 64-bit base address in canonical form into FS.base or GS.base using a single WRMSR instruction. The FS.base MSR address is C000_0100h while the GS.base MSR address is C000_0101h.
The second method of updating the FS and GS base fIElds is available to software running at any privilege level (when supported by the implementation and enabled by setting CR4[FSGSBASE]). The WRFSBASE and WRGSBASE instructions copy the contents of a GPR to the FS.base and GS.base fIElds respectively. When the operand size is 32 bits,the upper doubleword of the base is cleared. WRFSBASE and WRGSBASE are only supported in 64-bit mode.
以上是内存溢出为你收集整理的关于linux x86 64中MSR_GS_BASE的详细信息全部内容,希望文章能够帮你解决关于linux x86 64中MSR_GS_BASE的详细信息所遇到的程序开发问题。
如果觉得内存溢出网站内容还不错,欢迎将内存溢出网站推荐给程序员好友。
欢迎分享,转载请注明来源:内存溢出

 微信扫一扫
微信扫一扫
 支付宝扫一扫
支付宝扫一扫
评论列表(0条)