我已经为数据包的所有可能状态转换添加了iptables’-j LOG’规则,试图追踪它.我看到的数据包是:
>表’raw’,链PREROUTING
>表’mangle’,链PREROUTING
> table’nat’,链条PREROUTING
然后……没什么.在一小段延迟之后,数据包被重新发送,我看到新数据包通过PREROUTING.没有任何东西出现在剪辑input或mangle FORWARD链上 – 据我所知,这是不可能的 – 它必须击中其中一个.
有没有办法让数据包通过PREROUTING,但不能点击input或FORWARD?
我的iptables如下:
root@87ff7ad8e4f9:/# iptables -t raw -L Chain PREROUTING (policy ACCEPT)target prot opt source destination NFLOG tcp -- anywhere anywhere tcp spt:http-alt nflog-prefix "raw pre-route Src incoming packet"NFLOG tcp -- anywhere anywhere tcp dpt:http-alt nflog-prefix "raw pre-route Dest incoming packet"Chain OUTPUT (policy ACCEPT)target prot opt source destination NFLOG tcp -- anywhere anywhere tcp dpt:http-alt nflog-prefix "Dest outgoing packet"NFLOG tcp -- anywhere anywhere tcp spt:http-alt nflog-prefix "Src outgoing packet"root@87ff7ad8e4f9:/# iptables -t mangle -L Chain PREROUTING (policy ACCEPT)target prot opt source destination NFLOG tcp -- anywhere anywhere tcp dpt:http-alt nflog-prefix "mangle PREROUTING Dest incoming packet"Chain input (policy ACCEPT)target prot opt source destination NFLOG all -- anywhere anywhere nflog-prefix "mangle input Dest incoming packet any2"Chain FORWARD (policy ACCEPT)target prot opt source destination NFLOG all -- anywhere anywhere nflog-prefix "mangle FORWARD Dest incoming packet any"Chain OUTPUT (policy ACCEPT)target prot opt source destination MARK tcp -- anywhere anywhere tcp spt:http-alt MARK set 0x1MARK tcp -- anywhere anywhere tcp dpt:http-alt MARK set 0x1NFLOG tcp -- anywhere anywhere tcp spt:http-alt nflog-prefix "MARK set 0x1"NFLOG tcp -- anywhere anywhere tcp dpt:http-alt nflog-prefix "Dest MARK set 0x1"Chain POSTROUTING (policy ACCEPT)target prot opt source destination root@87ff7ad8e4f9:/# iptables -t nat -L Chain PREROUTING (policy ACCEPT)target prot opt source destination NFLOG tcp -- anywhere anywhere tcp dpt:http-alt nflog-prefix "nat PREROUTING Dest incoming packet"Chain input (policy ACCEPT)target prot opt source destination NFLOG tcp -- anywhere anywhere tcp dpt:http-alt nflog-prefix "nat input Dest incoming packet"Chain OUTPUT (policy ACCEPT)target prot opt source destination Chain POSTROUTING (policy ACCEPT)target prot opt source destination root@87ff7ad8e4f9:/# iptables -t filter -L Chain input (policy ACCEPT)target prot opt source destination NFLOG tcp -- anywhere anywhere nflog-prefix "connection made"NFLOG tcp -- anywhere anywhere tcp dpt:http-alt nflog-prefix "filter input Dest incoming packet"Chain FORWARD (policy ACCEPT)target prot opt source destination Chain OUTPUT (policy ACCEPT)target prot opt source destination ACCEPT all -- anywhere anywhere ctstate RELATED,ESTABliSHEDACCEPT all -- anywhere anywhere ACCEPT all -- anywhere anywhere ACCEPT all -- anywhere anywhere ACCEPT all -- anywhere 172.17.0.0/16 ACCEPT udp -- anywhere anywhere udp dpt:domainACCEPT tcp -- anywhere anywhere owner GID match vpnACCEPT udp -- anywhere anywhere owner GID match vpnDROP all -- anywhere anywhere
我的系统日志显示:
Oct 4 07:22:56 87ff7ad8e4f9 raw pre-route Dest incoming packet IN=eth0 OUT= MAC=02:42:ac:11:00:02:02:42:2e:2c:fd:2e:08:00 SRC=76.167.254.196 DST=172.17.0.2 LEN=60 TOS=00 PREC=0x00 TTL=63 ID=39119 DF PROTO=TCP SPT=46644 DPT=8080 SEQ=4027056663 ACK=0 WINDOW=29200 SYN URGP=0 MARK=0 Oct 4 07:22:56 87ff7ad8e4f9 mangle PREROUTING Dest incoming packet IN=eth0 OUT= MAC=02:42:ac:11:00:02:02:42:2e:2c:fd:2e:08:00 SRC=76.167.254.196 DST=172.17.0.2 LEN=60 TOS=00 PREC=0x00 TTL=63 ID=39119 DF PROTO=TCP SPT=46644 DPT=8080 SEQ=4027056663 ACK=0 WINDOW=29200 SYN URGP=0 MARK=0 Oct 4 07:22:56 87ff7ad8e4f9 nat PREROUTING Dest incoming packet IN=eth0 OUT= MAC=02:42:ac:11:00:02:02:42:2e:2c:fd:2e:08:00 SRC=76.167.254.196 DST=172.17.0.2 LEN=60 TOS=00 PREC=0x00 TTL=63 ID=39119 DF PROTO=TCP SPT=46644 DPT=8080 SEQ=4027056663 ACK=0 WINDOW=29200 SYN URGP=0 MARK=0 Oct 4 07:22:57 87ff7ad8e4f9 raw pre-route Dest incoming packet IN=eth0 OUT= MAC=02:42:ac:11:00:02:02:42:2e:2c:fd:2e:08:00 SRC=76.167.254.196 DST=172.17.0.2 LEN=60 TOS=00 PREC=0x00 TTL=63 ID=39120 DF PROTO=TCP SPT=46644 DPT=8080 SEQ=4027056663 ACK=0 WINDOW=29200 SYN URGP=0 MARK=0 Oct 4 07:22:57 87ff7ad8e4f9 mangle PREROUTING Dest incoming packet IN=eth0 OUT= MAC=02:42:ac:11:00:02:02:42:2e:2c:fd:2e:08:00 SRC=76.167.254.196 DST=172.17.0.2 LEN=60 TOS=00 PREC=0x00 TTL=63 ID=39120 DF PROTO=TCP SPT=46644 DPT=8080 SEQ=4027056663 ACK=0 WINDOW=29200 SYN URGP=0 MARK=0 Oct 4 07:22:57 87ff7ad8e4f9 nat PREROUTING Dest incoming packet IN=eth0 OUT= MAC=02:42:ac:11:00:02:02:42:2e:2c:fd:2e:08:00 SRC=76.167.254.196 DST=172.17.0.2 LEN=60 TOS=00 PREC=0x00 TTL=63 ID=39120 DF PROTO=TCP SPT=46644 DPT=8080 SEQ=4027056663 ACK=0 WINDOW=29200 SYN URGP=0 MARK=0解决方法 我想我明白了.
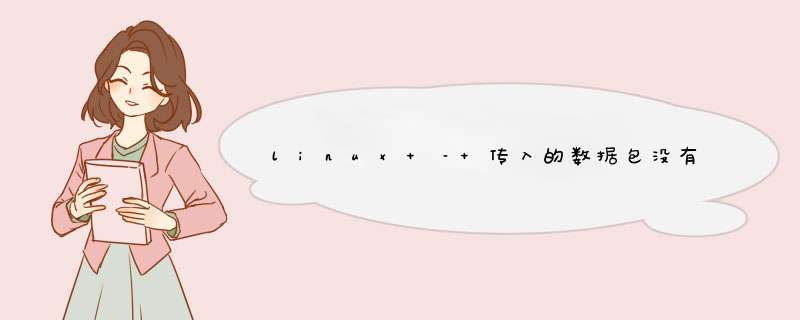
PREROUTING和input / FORWARD之间有什么关系?看看 the map:路由决策.
从您的日志:SRC = 76.167.254.196 DST = 172.17.0.2.
没有DNAT,您无法将公共路由到私有IP地址.尝试添加:
iptables -t nat -A PREROUTING -i eth0 -p tcp --dport 8080 -j DNAT --to-destination 172.17.0.2
或者您可以将VPN设置为拥有私有IP.
总结以上是内存溢出为你收集整理的linux – 传入的数据包没有命中iptables INPUT链全部内容,希望文章能够帮你解决linux – 传入的数据包没有命中iptables INPUT链所遇到的程序开发问题。
如果觉得内存溢出网站内容还不错,欢迎将内存溢出网站推荐给程序员好友。
欢迎分享,转载请注明来源:内存溢出

 微信扫一扫
微信扫一扫
 支付宝扫一扫
支付宝扫一扫
评论列表(0条)