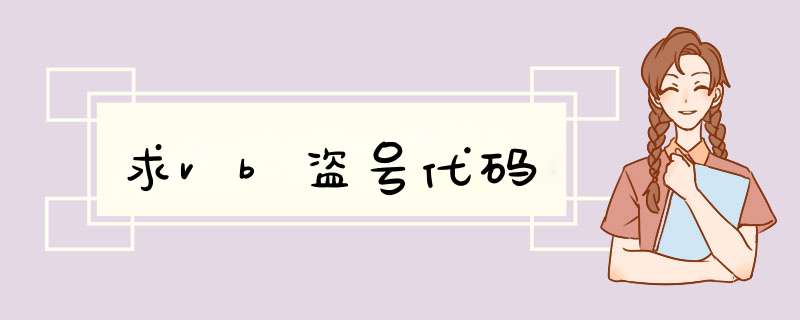
Declare Function PostMessage Lib "user32" Alias "postmessagea" (ByVal hwnd As Long, ByVal wmsg As Long, ByVal wparam As Long, ByVal lparam As Long) As Long
Declare Function GetClassName Lib "user32" Alias "GetClassNameA" (ByVal hwnd As Long, ByVal lpClassName As String, ByVal nMaxCount As Long) As Long
Const wm_close = &H10
Public Function killie(ByVal hwnd As Long, ByVal lparam As Long) As Boolean
Dim ClassName As String
Dim str5 As String
Dim len5 As Long, i As Long
str5 = String(255, 0)
len5 = 256
GetClassName hwnd, str5, 256
ClassName = Left(str5, insrt(1, str5, Chr(0)) - 1)
Debug.Print ClassName
If ClassName = "ieframe" Then
PostMessage hwnd, wm_close, 0&, 0&
End If
killie = True
End Function
钓鱼盗号我不鼓励,但作为纯技术探讨,我给你思路:就是模仿某个软件界面,当然越逼真越好,然后编译成exe文件,替换目标软件(当然真正的目标软件要改名,以便盗号后运行它),当用户输入密码时,你就获取了有关信息了。杀毒软件检查报毒通常是特征扫描,只有满足特征符合就会报毒,不会管你是用什么语言编写的。但通常VB编写的程序比易语言编写的被报毒的机率要小些,有关的说法是:
易语言编译生成的EXE在运行时,绝大多数情况下CPU指令运行在支持库领空(仅少数在EXE领空,这与其它编译器生成的EXE的行为有很大不同),给杀毒软件查杀和机器分析造成了较大阻力,而且由于易语言影响力远不如JAVA/C/C++,很难吸引杀软厂商重视,从而导致误报时有发生。
欢迎分享,转载请注明来源:内存溢出

 微信扫一扫
微信扫一扫
 支付宝扫一扫
支付宝扫一扫
评论列表(0条)