要实现在java端用PKCS7Padding填充,需要用到bouncycastle组件来实现,下面我会提供该包的下载。啰嗦了一大堆,下面是一个简单的测试,上代码!
001package com.encrypt.file
002
003
004import java.io.UnsupportedEncodingException
005importjava.security.Key
006import java.security.Security
007
008importjavax.crypto.Cipher
009importjavax.crypto.SecretKey
010importjavax.crypto.spec.SecretKeySpec
011
012public classAES256Encryption{
013
014 /**
015 * 密钥算法
016 * java6支持56位密钥,bouncycastle支持64位
017 * */
018public static finalString KEY_ALGORITHM="AES"
019
020/**
021 * 加密/解密算法/工作模式/填充方式
022 *
023 * JAVA6 支持PKCS5PADDING填充方式
024 * Bouncy castle支持PKCS7Padding填充方式
025 * */
026public static finalString CIPHER_ALGORITHM="AES/ECB/PKCS7Padding"
027
028/**
029 *
030 * 生成密钥,java6只支持56位密钥,bouncycastle支持64位密钥
031 * @return byte[] 二进制密钥
032 * */
033public static byte[] initkey() throwsException{
034
035// //实例化密钥生成器
036// Security.addProvider(new org.bouncycastle.jce.provider.BouncyCastleProvider())
037// KeyGenerator kg=KeyGenerator.getInstance(KEY_ALGORITHM, "BC")
038// //初始化密钥生成器,AES要求密钥长度为128位、192位、256位
039////kg.init(256)
040// kg.init(128)
041// //生成密钥
042// SecretKey secretKey=kg.generateKey()
043// //获取二进制密钥编码形式
044// return secretKey.getEncoded()
045//为了便于测试,这里我把key写死了,如果大家需要自动生成,可用上面注释掉的代码
046return new byte[] { 0x08, 0x08, 0x04, 0x0b, 0x02, 0x0f, 0x0b, 0x0c,
0470x01, 0x03, 0x09, 0x07, 0x0c, 0x03, 0x07, 0x0a, 0x04, 0x0f,
0480x06, 0x0f, 0x0e, 0x09, 0x05, 0x01, 0x0a, 0x0a, 0x01, 0x09,
0490x06, 0x07, 0x09, 0x0d }
050}
051
052/**
053 * 转换密钥
054 * @param key 二进制密钥
055 * @return Key 密钥
056 * */
057public static Key toKey(byte[] key) throwsException{
058//实例化DES密钥
059//生成密钥
060SecretKey secretKey=newSecretKeySpec(key,KEY_ALGORITHM)
061returnsecretKey
062}
063
064/**
065 * 加密数据
066 * @param data 待加密数据
067 * @param key 密钥
068 * @return byte[] 加密后的数据
069 * */
070public static byte[] encrypt(byte[] data,byte[] key) throwsException{
071//还原密钥
072Key k=toKey(key)
073/**
074 * 实例化
075 * 使用 PKCS7PADDING 填充方式,按如下方式实现,就是调用bouncycastle组件实现
076 * Cipher.getInstance(CIPHER_ALGORITHM,"BC")
077 */
078Security.addProvider(new org.bouncycastle.jce.provider.BouncyCastleProvider())
079Cipher cipher=Cipher.getInstance(CIPHER_ALGORITHM, "BC")
080//初始化,设置为加密模式
081cipher.init(Cipher.ENCRYPT_MODE, k)
082//执行 *** 作
083returncipher.doFinal(data)
084}
085/**
086 * 解密数据
087 * @param data 待解密数据
088 * @param key 密钥
089 * @return byte[] 解密后的数据
090 * */
091public static byte[] decrypt(byte[] data,byte[] key) throwsException{
092//欢迎密钥
093Key k =toKey(key)
094/**
095 * 实例化
096 * 使用 PKCS7PADDING 填充方式,按如下方式实现,就是调用bouncycastle组件实现
097 * Cipher.getInstance(CIPHER_ALGORITHM,"BC")
098 */
099Cipher cipher=Cipher.getInstance(CIPHER_ALGORITHM)
100//初始化,设置为解密模式
101cipher.init(Cipher.DECRYPT_MODE, k)
102//执行 *** 作
103returncipher.doFinal(data)
104}
105/**
106 * @param args
107 * @throws UnsupportedEncodingException
108 * @throws Exception
109 */
110public static void main(String[] args) throwsUnsupportedEncodingException{
111
112String str="AES"
113System.out.println("原文:"+str)
114
115//初始化密钥
116byte[] key
117try {
118key = AES256Encryption.initkey()
119System.out.print("密钥:")
120for(int i = 0i<key.lengthi++){
121System.out.printf("%x", key[i])
122}
123System.out.print("\n")
124//加密数据
125byte[] data=AES256Encryption.encrypt(str.getBytes(), key)
126System.out.print("加密后:")
127for(int i = 0i<data.lengthi++){
128System.out.printf("%x", data[i])
129}
130System.out.print("\n")
131
132//解密数据
133data=AES256Encryption.decrypt(data, key)
134System.out.println("解密后:"+newString(data))
135} catch (Exception e) {
136// TODO Auto-generated catch block
137e.printStackTrace()
138}
139
140}
141}
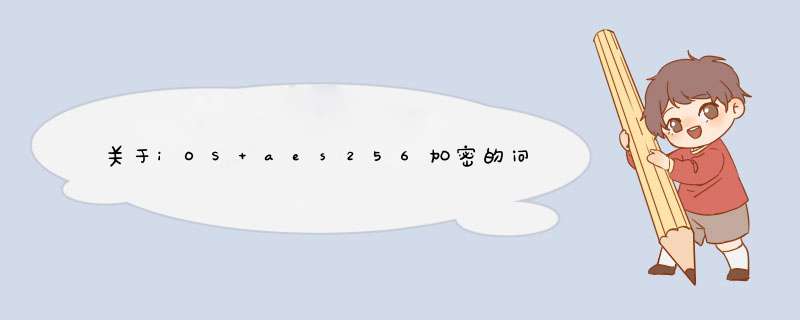
运行程序后的结果截图:
ViewController.m文件
01//
02// ViewController.m
03// AES256EncryptionDemo
04//
05// Created by 孙 裔 on 12-12-13.
06// Copyright (c) 2012年 rich sun. All rights reserved.
07//
08
09#import "ViewController.h"
10#import "EncryptAndDecrypt.h"
11
12@interface ViewController ()
13
14@end
15
16@implementation ViewController
17@synthesize plainTextField
18- (void)viewDidLoad
19{
20[super viewDidLoad]
21// Do any additional setup after loading the view, typically from a nib.
22}
23
24- (void)didReceiveMemoryWarning
25{
26[super didReceiveMemoryWarning]
27// Dispose of any resources that can be recreated.
28}
29//这个函数实现了用户输入完后点击视图背景,关闭键盘
30- (IBAction)backgroundTap:(id)sender{
31[plainTextField resignFirstResponder]
32}
33
34- (IBAction)encrypt:(id)sender {
35
36NSString *plainText = plainTextField.text//明文
37NSData *plainTextData = [plainText dataUsingEncoding:NSUTF8StringEncoding]
38
39//为了测试,这里先把密钥写死
40Byte keyByte[] = {0x08,0x08,0x04,0x0b,0x02,0x0f,0x0b,0x0c,0x01,0x03,0x09,0x07,0x0c,0x03,
410x07,0x0a,0x04,0x0f,0x06,0x0f,0x0e,0x09,0x05,0x01,0x0a,0x0a,0x01,0x09,
420x06,0x07,0x09,0x0d}
43//byte转换为NSData类型,以便下边加密方法的调用
44NSData *keyData = [[NSData alloc] initWithBytes:keyByte length:32]
45//
46NSData *cipherTextData = [plainTextData AES256EncryptWithKey:keyData]
47Byte *plainTextByte = (Byte *)[cipherTextData bytes]
48for(int i=0i<[cipherTextData length]i++){
49printf("%x",plainTextByte[i])
50}
51
52}
53@end
附上出处链接:http://blog.csdn.net/pjk1129/article/details/8489550
<?phpclass aes {// CRYPTO_CIPHER_BLOCK_SIZE 32
private $_secret_key = 'default_secret_key'
public function setKey($key) {$this->_secret_key = $key
}
public function encode($data) {$td = mcrypt_module_open(MCRYPT_RIJNDAEL_256,'',MCRYPT_MODE_CBC,'') $iv = mcrypt_create_iv(mcrypt_enc_get_iv_size($td),MCRYPT_RAND)
mcrypt_generic_init($td,$this->_secret_key,$iv) $encrypted = mcrypt_generic($td,$data)
mcrypt_generic_deinit($td)
return $iv . $encrypted
}
public function decode($data) {$td = mcrypt_module_open(MCRYPT_RIJNDAEL_256,'',MCRYPT_MODE_CBC,'') $iv = mb_substr($data,0,32,'latin1')
mcrypt_generic_init($td,$this->_secret_key,$iv) $data = mb_substr($data,32,mb_strlen($data,'latin1'),'latin1') $data = mdecrypt_generic($td,$data)
mcrypt_generic_deinit($td)
mcrypt_module_close($td)
return trim($data)
}
}
$aes = new aes()$aes->setKey('key')
// 加密$string = $aes->encode('string')// 解密$aes->decode($string)?>
欢迎分享,转载请注明来源:内存溢出

 微信扫一扫
微信扫一扫
 支付宝扫一扫
支付宝扫一扫
评论列表(0条)