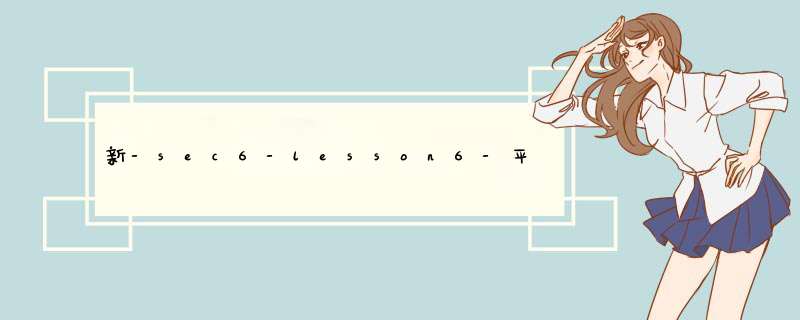
package com.sam.myapplicationcj;
import android.util.Log;
import com.virjar.ratel.api.rposed.IRposedHookLoadPackage;
import com.virjar.ratel.api.rposed.RC_MethodHook;
import com.virjar.ratel.api.rposed.RposedHelpers;
import com.virjar.ratel.api.rposed.callbacks.RC_LoadPackage;
import java.math.BigInteger;
import java.security.MessageDigest;
import javax.crypto.Cipher;
import javax.crypto.spec.IvParameterSpec;
import javax.crypto.spec.SecretKeySpec;
public class HookCryptoEntry implements IRposedHookLoadPackage {
private static final String TAG = "yuanrenxue->";
@Override
public void handleLoadPackage(RC_LoadPackage.LoadPackageParam lpparam) throws Throwable {
if("com.yuanrenxue.course6".equals(lpparam.packageName)){
Log.d(TAG, "handleLoadPackage: hook success");
// 想hook这个:new SecretKeySpec(key.getBytes(),"AES");这里用的是findAndHookConstructor因为new ... 就是一个
// 实例化的过程,所以需要hook的是构造方法而不是普通方法
RposedHelpers.findAndHookConstructor(SecretKeySpec.class, byte[].class, String.class, new RC_MethodHook() {
@Override
protected void afterHookedMethod(MethodHookParam param) throws Throwable {
super.afterHookedMethod(param);
Log.d(TAG, String.format("SecretKeySpec(%s,%s))",new String((byte[]) param.args[0]),param.args[1]));
}
});
// hook iv:new IvParameterSpec(iv.getBytes());
RposedHelpers.findAndHookConstructor(IvParameterSpec.class, byte[].class, new RC_MethodHook() {
@Override
protected void afterHookedMethod(MethodHookParam param) throws Throwable {
super.afterHookedMethod(param);
Log.d(TAG, String.format("IvParameterSpec(%s)",new String((byte[]) param.args[0])));
}
});
// hook 采用了什么加密算法:Cipher.getInstance("AES/CBC/PKCS5Padding")
RposedHelpers.findAndHookMethod(Cipher.class, "getInstance", String.class, new RC_MethodHook() {
@Override
protected void afterHookedMethod(MethodHookParam param) throws Throwable {
super.afterHookedMethod(param);
Log.d(TAG, "发现使用如下加密算法: " + param.args[0]);
}
});
// hook 加密解密过程:cipher.doFinal(content.getBytes());
RposedHelpers.findAndHookMethod(Cipher.class, "doFinal", byte[].class, new RC_MethodHook() {
@Override
protected void afterHookedMethod(MethodHookParam param) throws Throwable {
super.afterHookedMethod(param);
// 对于加密来说:入参(明文),返回值(密文)
// 对于解密来说:入参(密文),返回值(明文) 可以通过这来判断在加密还是在解密
// 加密的返回值因为是随机的字节,所以打印出来很可能是鬼画符一样的东西�7sZ������O��像这种,是正常的
Log.d(TAG, String.format("入参为:%s,返回值为:%s",new String((byte[])param.args[0]),new String((byte[])param.getResult())));
}
});
// hook采用了哪种哈希函数(摘要算法) MessageDigest.getInstance("MD5");
RposedHelpers.findAndHookMethod(MessageDigest.class, "getInstance", String.class, new RC_MethodHook() {
@Override
protected void afterHookedMethod(MethodHookParam param) throws Throwable {
super.afterHookedMethod(param);
Log.d(TAG, "发现使用如下哈希函数: " + param.args[0]);
}
});
// 对于摘要内容的hook
// 1. md.digest(content.getBytes());
RposedHelpers.findAndHookMethod(MessageDigest.class, "digest", byte[].class, new RC_MethodHook() {
@Override
protected void afterHookedMethod(MethodHookParam param) throws Throwable {
super.afterHookedMethod(param);
Log.d(TAG, "消息内容为: " + new String((byte[]) param.args[0]));
Log.d(TAG, "摘要结果为: " + new String((byte[]) param.getResult()));
Log.d(TAG, "摘要结果为: " + new BigInteger(1, (byte[]) param.getResult()).toString(16));
}
});
// 2. md.update(content.getBytes());
RposedHelpers.findAndHookMethod(MessageDigest.class, "update", byte[].class, new RC_MethodHook() {
@Override
protected void afterHookedMethod(MethodHookParam param) throws Throwable {
super.afterHookedMethod(param);
Log.d(TAG, "2.消息内容为: " + new String((byte[]) param.args[0]));
}
});
RposedHelpers.findAndHookMethod(MessageDigest.class, "digest",new RC_MethodHook() {
@Override
protected void afterHookedMethod(MethodHookParam param) throws Throwable {
super.afterHookedMethod(param);
Log.d(TAG, "2.摘要结果为: " + new BigInteger(1, (byte[]) param.getResult()).toString(16));
}
});
}
}
}
一些param.getresult结果直接转string是乱码
Java 中的 [B@4a5ab2 是什么?
Object 默认的toString 返回的内容 是从内存地址计算出来的一个数值 没有什么实际意义 可以作为对象的唯一ID一个汉字在utf编码中占3个字节 Java 字节数组和字符串的互转
String str = "虎虎生威";
byte[] sb = str.getBytes();
System.out.println(Arrays.toString(sb));
System.out.println("------------");
System.out.println(new String(sb));
System.out.println("------------");
byte[] t={-24, -103, -114, -24, -103, -114, -25, -108, -97, -27, -88, -127};
String str1= new String (t);
System.out.println(str1);
插件是E:1A_androidstudio_projectproject_save
APP是E:1A_androidstudio_projectCourseSix
欢迎分享,转载请注明来源:内存溢出

 微信扫一扫
微信扫一扫
 支付宝扫一扫
支付宝扫一扫
评论列表(0条)