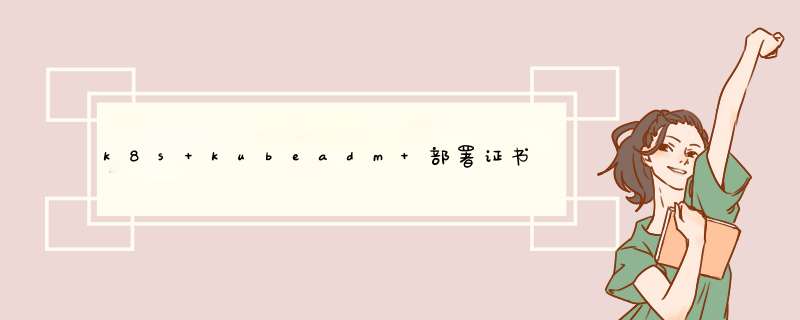
k8s 证书分为2套,一套是apiserver 和etcd
管理节点:如果是kubeadm 部署则自动生成,二进制一般由cfssl 或者openssl
工作节点: 工作节点主要指kubelet 连接apiserver 所需的客户端证书,这个证书是由controller-manager组件自动颁发,默认是一年,如果到期,kubelet 将无法使用过期的证书连接apiserver,日志将会报错 (x509:certificate has expired or is not yet valid)
红线:k8s 自建证书颁发机构CA ,需携带由他生成的客户端证书访问apiserver
蓝线:ETCD 自建证书颁发机构CA,需携带由他生成的客户端证书访问TECD
root@k8s-master:/etc/kubernetes/pki/etcd# for item in `find /etc/kubernetes/pki -maxdepth 2 -name "*.crt"`;do openssl x509 -in $item -text -noout| grep Not;echo ======================$item===============;done
Not Before: Jan 26 03:19:19 2022 GMT
Not After : Jan 26 03:19:20 2023 GMT
======================/etc/kubernetes/pki/apiserver-kubelet-client.crt===============
Not Before: Jan 26 03:19:19 2022 GMT
Not After : Jan 24 03:19:19 2032 GMT
======================/etc/kubernetes/pki/ca.crt===============
Not Before: Jan 26 03:19:20 2022 GMT
Not After : Jan 26 03:19:20 2023 GMT
======================/etc/kubernetes/pki/front-proxy-client.crt===============
Not Before: Jan 26 03:19:19 2022 GMT
Not After : Jan 26 03:19:20 2023 GMT
======================/etc/kubernetes/pki/apiserver.crt===============
Not Before: Jan 26 03:19:21 2022 GMT
Not After : Jan 24 03:19:21 2032 GMT
======================/etc/kubernetes/pki/etcd/ca.crt===============
Not Before: Jan 26 03:19:21 2022 GMT
Not After : Jan 26 03:19:22 2023 GMT
======================/etc/kubernetes/pki/etcd/server.crt===============
Not Before: Jan 26 03:19:21 2022 GMT
Not After : Jan 26 03:19:22 2023 GMT
======================/etc/kubernetes/pki/etcd/peer.crt===============
Not Before: Jan 26 03:19:21 2022 GMT
Not After : Jan 26 03:19:22 2023 GMT
======================/etc/kubernetes/pki/etcd/healthcheck-client.crt===============
Not Before: Jan 26 03:19:21 2022 GMT
Not After : Jan 26 03:19:23 2023 GMT
======================/etc/kubernetes/pki/apiserver-etcd-client.crt===============
Not Before: Jan 26 03:19:20 2022 GMT
Not After : Jan 24 03:19:20 2032 GMT
======================/etc/kubernetes/pki/front-proxy-ca.crt===============
方法:
1,官方的办法:一年之内kubeadm upgrade 升级一次k8s 集群版本
2,民间方法:修改源码
3,手动更新证书:(kubeadm alpha phase certs)
开始配置:
新增2行
vim /etc/kubernetes/manifests/kube-controller-manager.yaml - --experimental-cluster-signing-duration=87600h0m0s - --feature-gates=RotateKubeletServerCertificate=true
root@k8s-master:/etc/kubernetes/pki# kubectl delete pods kube-controller-manager-k8s-master -n kube-system pod "kube-controller-manager-k8s-master" deleted
vim /var/lib/kubelet/config.yaml rotateCertificates: true
systemctl restart kubelet
查看
root@k8s-master:/etc/kubernetes/pki# openssl x509 -in ca.crt --noout -dates notBefore=Jan 26 03:19:19 2022 GMT notAfter=Jan 24 03:19:19 2032 GMT查看证书截止时间,该命令显示 /etc/kubernetes/pki 文件夹中的客户端证书以及 kubeadm 使用的 KUBEConFIG 文件中嵌入的客户端证书的到期时间/剩余时间。新版本命令:kubeadm certs check-expiration kubeadm alpha certs check-expiration
root@k8s-master:~# kubeadm certs check-expiration [check-expiration] Reading configuration from the cluster... [check-expiration] FYI: You can look at this config file with 'kubectl -n kube-system get cm kubeadm-config -o yaml' CERTIFICATE EXPIRES RESIDUAL TIME CERTIFICATE AUTHORITY EXTERNALLY MANAGED admin.conf Jan 26, 2023 03:19 UTC 355d no apiserver Jan 26, 2023 03:19 UTC 355d ca no apiserver-etcd-client Jan 26, 2023 03:19 UTC 355d etcd-ca no apiserver-kubelet-client Jan 26, 2023 03:19 UTC 355d ca no controller-manager.conf Jan 26, 2023 03:19 UTC 355d no etcd-healthcheck-client Jan 26, 2023 03:19 UTC 355d etcd-ca no etcd-peer Jan 26, 2023 03:19 UTC 355d etcd-ca no etcd-server Jan 26, 2023 03:19 UTC 355d etcd-ca no front-proxy-client Jan 26, 2023 03:19 UTC 355d front-proxy-ca no scheduler.conf Jan 26, 2023 03:19 UTC 355d no CERTIFICATE AUTHORITY EXPIRES RESIDUAL TIME EXTERNALLY MANAGED ca Jan 24, 2032 03:19 UTC 9y no etcd-ca Jan 24, 2032 03:19 UTC 9y no front-proxy-ca Jan 24, 2032 03:19 UTC 9y no重新生成证书
kubeadm alpha certs renew all
新版命令
root@k8s-master:~# kubeadm certs renew all [renew] Reading configuration from the cluster... [renew] FYI: You can look at this config file with 'kubectl -n kube-system get cm kubeadm-config -o yaml' certificate embedded in the kubeconfig file for the admin to use and for kubeadm itself renewed certificate for serving the Kubernetes API renewed certificate the apiserver uses to access etcd renewed certificate for the API server to connect to kubelet renewed certificate embedded in the kubeconfig file for the controller manager to use renewed certificate for liveness probes to healthcheck etcd renewed certificate for etcd nodes to communicate with each other renewed certificate for serving etcd renewed certificate for the front proxy client renewed certificate embedded in the kubeconfig file for the scheduler manager to use renewed Done renewing certificates. You must restart the kube-apiserver, kube-controller-manager, kube-scheduler and etcd, so that they can use the new certificates.
欢迎分享,转载请注明来源:内存溢出

 微信扫一扫
微信扫一扫
 支付宝扫一扫
支付宝扫一扫
评论列表(0条)