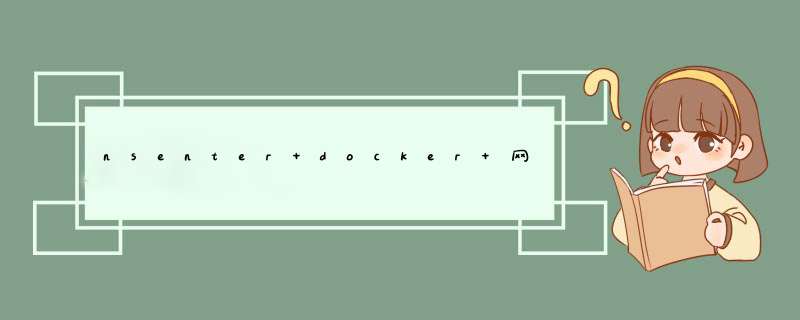
docker run --name nginx -d -p 8080:80 nginx
# Or docker top 获取进程ID
# 启动shell进程进入容器的UTS 和 NET 命名空间
sudo nsenter -t $(docker inspect --format '{{.State.Pid}}' nginx) -u -n
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
9: eth0@if10: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default
link/ether 02:42:ac:11:00:02 brd ff:ff:ff:ff:ff:ff link-netnsid 0
inet 172.17.0.2/16 brd 172.17.255.255 scope global eth0
valid_lft forever preferred_lft forever
; <<>> DiG 9.16.11-Debian <<>> www.baidu.com
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: FORMERR, id: 4630
;; flags: qr rd; QUERY: 1, ANSWER: 0, AUTHORITY: 0, ADDITIONAL: 1
;; WARNING: recursion requested but not available
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; MBZ: 0x0005, udp: 4096
; COOKIE: 3cceebd190c4512c (echoed)
;; QUESTION SECTION:
;www.baidu.com. IN A
;; Query time: 8 msec
;; SERVER: 172.25.1.2#53(172.25.1.2)
;; WHEN: 一 5月 09 10:53:04 CST 2022
;; MSG SIZE rcvd: 54
Active Internet connections (servers and established)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 0.0.0.0:80 0.0.0.0:* LISTEN 5464/nginx: master
tcp6 0 0 :::80 :::* LISTEN 5464/nginx: master
tcpdump: verbose output suppressed, use -v[v]... for full protocol decode
listening on eth0, link-type EN10MB (Ethernet), snapshot length 262144 bytes
11:15:31.370632 IP 172.17.0.1.53018 > 172.17.0.2.http: Flags [S], seq 1202746632, win 64240, options [mss 1460,sackOK,TS val 3128309799 ecr 0,nop,wscale 7], length 0
11:15:31.370647 IP 172.17.0.2.http > 172.17.0.1.53018: Flags [S.], seq 2585287573, ack 1202746633, win 65160, options [mss 1460,sackOK,TS val 1354911818 ecr 3128309799,nop,wscale 7], length 0
11:15:31.370675 IP 172.17.0.1.53018 > 172.17.0.2.http: Flags [.], ack 1, win 502, options [nop,nop,TS val 3128309799 ecr 1354911818], length 0
11:15:31.371046 IP 172.17.0.1.53018 > 172.17.0.2.http: Flags [P.], seq 1:433, ack 1, win 502, options [nop,nop,TS val 3128309799 ecr 1354911818], length 432: HTTP: GET / HTTP/1.1
11:15:31.371076 IP 172.17.0.2.http > 172.17.0.1.53018: Flags [.], ack 433, win 506, options [nop,nop,TS val 1354911819 ecr 3128309799], length 0
11:15:31.371277 IP 172.17.0.2.http > 172.17.0.1.53018: Flags [P.], seq 1:181, ack 433, win 506, options [nop,nop,TS val 1354911819 ecr 3128309799], length 180: HTTP: HTTP/1.1 304 Not Modified
11:15:31.371303 IP 172.17.0.1.53018 > 172.17.0.2.http: Flags [.], ack 181, win 501, options [nop,nop,TS val 3128309800 ecr 1354911819], length 0
欢迎分享,转载请注明来源:内存溢出

 微信扫一扫
微信扫一扫
 支付宝扫一扫
支付宝扫一扫
评论列表(0条)