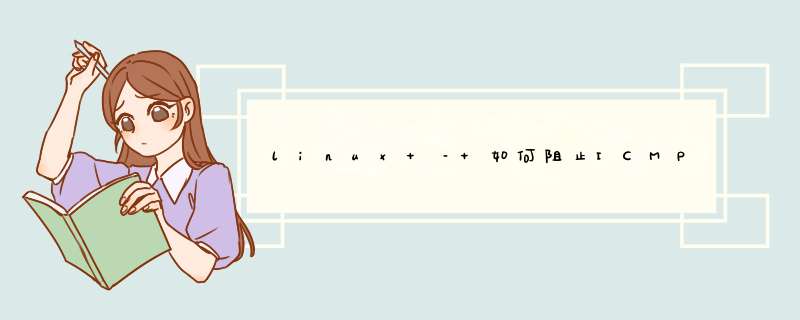
[root@server downloads]# tcpdump icmp -v -n -nntcpdump: Listening on eth0,link-type EN10MB (Ethernet),capture size 96 bytes03:02:47.810957 IP (tos 0x0,ttl 49,ID 16007,offset 0,flags [none],proto: ICMP (1),length: 56) 80.227.64.183 > 77.92.136.196: ICMP redirect 94.201.175.188 to host 80.227.64.129,length 36 IP (tos 0x0,ttl 124,ID 31864,length: 76) 77.92.136.196 > 94.201.175.188: [|icmp]03:02:47.811559 IP (tos 0x0,ID 16010,ttl 52,length: 76) 77.92.136.196 > 94.201.175.188: [|icmp]03:02:47.811922 IP (tos 0x0,ID 16012,ttl 122,length: 76) 77.92.136.196 > 94.201.175.188: [|icmp]03:02:47.812485 IP (tos 0x0,ID 16015,ttl 126,length: 76) 77.92.136.196 > 94.201.175.188: [|icmp]03:02:47.812613 IP (tos 0x0,ID 16016,length: 76) 77.92.136.196 > 94.201.175.188: [|icmp]03:02:47.812992 IP (tos 0x0,ID 16018,length: 76) 77.92.136.196 > 94.201.175.188: [|icmp]03:02:47.813582 IP (tos 0x0,ID 16020,length: 76) 77.92.136.196 > 94.201.175.188: [|icmp]03:02:47.814092 IP (tos 0x0,ID 16023,ttl 120,length: 76) 77.92.136.196 > 94.201.175.188: [|icmp]03:02:47.814233 IP (tos 0x0,ID 16024,length: 76) 77.92.136.196 > 94.201.175.188: [|icmp]03:02:47.815579 IP (tos 0x0,ID 16025,ttl 50,length: 76) 77.92.136.196 > 94.201.175.188: [|icmp]03:02:47.815726 IP (tos 0x0,ID 16026,length: 76) 77.92.136.196 > 94.201.175.188: [|icmp]03:02:47.815890 IP (tos 0x0,ID 16027,length 36
iptables配置:
[root@server etc]# iptables -LChain input (policy ACCEPT)target prot opt source destinationofis tcp -- anywhere anywhere tcp dpt:MysqLofis tcp -- anywhere anywhere tcp dpt:ftpDROP icmp -- anywhere anywhereChain FORWARD (policy ACCEPT)target prot opt source destinationChain OUTPUT (policy ACCEPT)target prot opt source destinationDROP icmp -- anywhere anywhereChain ofis (2 references)target prot opt source destinationACCEPT all -- OUR_OFFICE_IP anywhereDROP all -- anywhere anywhere
最佳:
top - 03:12:19 up 400 days,15:43,3 users,load average: 1.49,1.67,2.61Tasks: 751 total,3 running,748 sleePing,0 stopped,0 zombIEcpu(s): 8.2%us,1.0%sy,0.0%ni,87.9%ID,2.1%wa,0.1%hi,0.7%si,0.0%stMem: 32949948k total,26906844k used,6043104k free,4707676k buffersSwap: 10223608k total,0k used,10223608k free,14255584k cached PID USER PR NI VIRT RES SHR S %cpu %MEM TIME+ COMMAND 36 root 39 19 0 0 0 R 100.8 0.0 17:03.56 ksoftirqd/1110552 root 15 0 11408 1460 676 R 5.7 0.0 0:00.04 top 7475 lighttpd 15 0 304m 22m 15m S 3.8 0.1 0:05.37 php-cgi 1294 root 10 -5 0 0 0 S 1.9 0.0 380:54.73 kjournald 3574 root 15 0 631m 11m 5464 S 1.9 0.0 0:00.65 node 7766 lighttpd 16 0 302m 19m 14m S 1.9 0.1 0:05.70 php-cgi10237 postfix 15 0 52572 2216 1692 S 1.9 0.0 0:00.02 scache 1 root 15 0 10372 680 572 S 0.0 0.0 0:07.99 init 2 root RT -5 0 0 0 S 0.0 0.0 0:16.72 migration/0 3 root 34 19 0 0 0 S 0.0 0.0 0:00.06 ksoftirqd/0 4 root RT -5 0 0 0 S 0.0 0.0 0:00.00 watchdog/0 5 root RT -5 0 0 0 S 0.0 0.0 1:10.46 migration/1 6 root 34 19 0 0 0 S 0.0 0.0 0:01.11 ksoftirqd/1 7 root RT -5 0 0 0 S 0.0 0.0 0:00.00 watchdog/1 8 root RT -5 0 0 0 S 0.0 0.0 2:36.15 migration/2 9 root 34 19 0 0 0 S 0.0 0.0 0:00.19 ksoftirqd/2 10 root RT -5 0 0 0 S 0.0 0.0 0:00.00 watchdog/2 11 root RT -5 0 0 0 S 0.0 0.0 3:48.91 migration/3 12 root 34 19 0 0 0 S 0.0 0.0 0:00.20 ksoftirqd/3 13 root RT -5 0 0 0 S 0.0 0.0 0:00.00 watchdog/3
uname -a
[root@server etc]# uname -alinux thisis.oursite.com 2.6.18-238.19.1.el5 #1 SMP Fri Jul 15 07:31:24 EDT 2011 x86_64 x86_64 x86_64 GNU/linux
arp -an
[root@server downloads]# arp -an? (77.92.136.194) at 00:25:90:04:F0:90 [ether] on eth0? (192.168.0.2) at 00:25:90:04:F0:91 [ether] on eth1? (77.92.136.193) at 00:23:9C:0B:CD:01 [ether] on eth0解决方法 联系您的ISP并向他们提供此信息.他们需要减少主干上的流量.一旦流量到达防火墙,资源就已经消耗掉了.阻止这种情况的唯一方法是将其放在主干上. 总结
以上是内存溢出为你收集整理的linux – 如何阻止ICMP攻击?全部内容,希望文章能够帮你解决linux – 如何阻止ICMP攻击?所遇到的程序开发问题。
如果觉得内存溢出网站内容还不错,欢迎将内存溢出网站推荐给程序员好友。
欢迎分享,转载请注明来源:内存溢出

 微信扫一扫
微信扫一扫
 支付宝扫一扫
支付宝扫一扫
评论列表(0条)