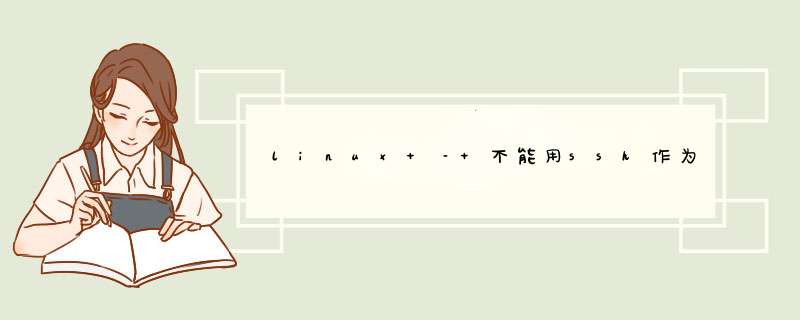
OpenSSH_5.9p1,OpenSSL 1.0.0g 18 Jan 2012Pseudo-terminal will not be allocated because stdin is not a terminal.deBUG1: Reading configuration data /etc/ssh/ssh_configdeBUG1: Connecting to localhost [::1] port 54367.deBUG1: Connection established.deBUG1: IDentity file nonpublic/ID_rsa type 1deBUG1: IDentity file nonpublic/ID_rsa-cert type -1deBUG1: Remote protocol version 2.0,remote software version OpenSSH_5.9deBUG1: match: OpenSSH_5.9 pat OpenSSH*deBUG1: Enabling compatibility mode for protocol 2.0deBUG1: Local version string SSH-2.0-OpenSSH_5.9deBUG1: SSH2_MSG_KEXINIT sentdeBUG1: SSH2_MSG_KEXINIT receiveddeBUG1: kex: server->clIEnt aes128-ctr hmac-md5 nonedeBUG1: kex: clIEnt->server aes128-ctr hmac-md5 nonedeBUG1: sending SSH2_MSG_KEX_ECDH_INITdeBUG1: expecting SSH2_MSG_KEX_ECDH_REPLYdeBUG1: Server host key: ECDSA e3:c2:37:8e:8b:d4:77:63:7f:d2:ba:12:e5:e9:d1:9adeBUG1: checking without port IDentifIErdeBUG1: read_passphrase: can't open /dev/tty: No such device or addressHost key verification @R_419_5138@.
调用ssh时设置-t标志.密钥没有密码,这应该可以抑制任何输入的需要,但显然它没有.如何阻止ssh尝试打开/ dev / tty?
编辑:代码标签不起作用?
Edit2:完整的ssh命令:
ssh -i nonpublic / ID_rsa -l username -p 54367 -t -v username @ localhost / home / username / minecraftserver / Scripts / start 2>& 1
我用“用户名”替换了我的用户名.
编辑3:我尝试使用与root相同的密钥进行ssh-ing并获得此结果:
OpenSSH_5.9p1,OpenSSL 1.0.0g 18 Jan 2012deBUG1: Reading configuration data /etc/ssh/ssh_configdeBUG1: Connecting to localhost [::1] port 54367.deBUG1: Connection established.deBUG1: permanently_set_uID: 0/0deBUG1: IDentity file /srv/http/nonpublic/ID_rsa type 1deBUG1: IDentity file /srv/http/nonpublic/ID_rsa-cert type -1deBUG1: Remote protocol version 2.0,remote software version OpenSSH_5.9deBUG1: match: OpenSSH_5.9 pat OpenSSH*deBUG1: Enabling compatibility mode for protocol 2.0deBUG1: Local version string SSH-2.0-OpenSSH_5.9deBUG1: SSH2_MSG_KEXINIT sentdeBUG1: SSH2_MSG_KEXINIT receiveddeBUG1: kex: server->clIEnt aes128-ctr hmac-md5 nonedeBUG1: kex: clIEnt->server aes128-ctr hmac-md5 nonedeBUG1: sending SSH2_MSG_KEX_ECDH_INITdeBUG1: expecting SSH2_MSG_KEX_ECDH_REPLYdeBUG1: Server host key: ECDSA e3:c2:37:8e:8b:d4:77:63:7f:d2:ba:12:e5:e9:d1:9adeBUG1: checking without port IDentifIErThe authenticity of host '[localhost]:54367 ([::1]:54367)' can't be established.ECDSA key fingerprint is e3:c2:37:8e:8b:d4:77:63:7f:d2:ba:12:e5:e9:d1:9a.Are you sure you want to continue connecting (yes/no)? yesWarning: Permanently added '[localhost]:54367' (ECDSA) to the List of kNown hosts.deBUG1: ssh_ecdsa_verify: signature correctdeBUG1: SSH2_MSG_NEWKEYS sentdeBUG1: expecting SSH2_MSG_NEWKEYSdeBUG1: SSH2_MSG_NEWKEYS receiveddeBUG1: Roaming not allowed by serverdeBUG1: SSH2_MSG_SERVICE_REQUEST sentdeBUG1: SSH2_MSG_SERVICE_ACCEPT receiveddeBUG1: Authentications that can continue: publickeydeBUG1: Next authentication method: publickeydeBUG1: Offering RSA public key: /srv/http/nonpublic/ID_rsadeBUG1: Server accepts key: pkalg ssh-rsa blen 279deBUG1: key_parse_private_pem: PEM_read_PrivateKey @R_419_5138@deBUG1: read PEM private key done: type <unkNown>Enter passphrase for key '/srv/http/nonpublic/ID_rsa':deBUG1: No more authentication methods to try.Permission denIEd (publickey).
它提示我输入密码,即使它不需要密码.此外,我可以使用密钥ssh在windows机器上使用PuTTY就好了,它不会提示我输入密码.
Edit4:我将服务器添加到apache用户kNown_hosts,现在我得到了这个:
OpenSSH_5.9p1,remote software version OpenSSH_5.9deBUG1: match: OpenSSH_5.9 pat OpenSSH*deBUG1: Enabling compatibility mode for protocol 2.0deBUG1: Local version string SSH-2.0-OpenSSH_5.9deBUG1: SSH2_MSG_KEXINIT sentdeBUG1: SSH2_MSG_KEXINIT receiveddeBUG1: kex: server->clIEnt aes128-ctr hmac-md5 nonedeBUG1: kex: clIEnt->server aes128-ctr hmac-md5 nonedeBUG1: sending SSH2_MSG_KEX_ECDH_INITdeBUG1: expecting SSH2_MSG_KEX_ECDH_REPLYdeBUG1: Server host key: ECDSA e3:c2:37:8e:8b:d4:77:63:7f:d2:ba:12:e5:e9:d1:9adeBUG1: Host '[localhost]:54367' is kNown and matches the ECDSA host key.deBUG1: Found key in /srv/http/.ssh/kNown_hosts:1deBUG1: ssh_ecdsa_verify: signature correctdeBUG1: SSH2_MSG_NEWKEYS sentdeBUG1: expecting SSH2_MSG_NEWKEYSdeBUG1: SSH2_MSG_NEWKEYS receiveddeBUG1: Roaming not allowed by serverdeBUG1: SSH2_MSG_SERVICE_REQUEST sentdeBUG1: SSH2_MSG_SERVICE_ACCEPT receiveddeBUG1: Authentications that can continue: publickeydeBUG1: Next authentication method: publickeydeBUG1: Offering RSA public key: nonpublic/ID_rsadeBUG1: Server accepts key: pkalg ssh-rsa blen 279deBUG1: key_parse_private_pem: PEM_read_PrivateKey @R_419_5138@deBUG1: read PEM private key done: typedeBUG1: read_passphrase: can't open /dev/tty: No such device or addressdeBUG1: No more authentication methods to try.Permission denIEd (publickey).`
另外,这是kNown_hosts的内容:
[localhost]:54367 ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBILr7jLp5CeYfyrCroaDjkaWgDHXRrQD+G8Fz/CQOY1PcluUFTkrN447bXmC6R27LOClE+RPaveYb4MolObpGGE=
为什么说ecdsa?这是一个关键.
编辑5:解决了.问题是密钥对是由PuTTY生成的,PuTTY以与OpenSSH不兼容的格式写入私钥. cjc在评论中提供的解决方案.
解决方法 问题实际上似乎并不是它试图读取密码 – 这只是一个警告.相反,它正在尝试进行主机密钥验证但失败了.如果您真的希望它永远不会询问主机密钥,请考虑将以下选项添加到ssh命令行:-o StrictHostKeyChecking=no -o UserKNownHostsfile=/dev/null -o GlobalKNownHostsfile=/dev/null
请注意,可能存在安全隐患,因此请务必在ssh_config手册页中阅读有关这些选项的信息.
编辑:鉴于您更新的错误消息,看起来您有一个损坏的身份文件(或cjc指出,它可能是错误的格式).尝试使用ssh-keygen手动创建一个新的,并将其添加到服务器的authorized_keys.
总结以上是内存溢出为你收集整理的linux – 不能用ssh作为tty-less用户全部内容,希望文章能够帮你解决linux – 不能用ssh作为tty-less用户所遇到的程序开发问题。
如果觉得内存溢出网站内容还不错,欢迎将内存溢出网站推荐给程序员好友。
欢迎分享,转载请注明来源:内存溢出

 微信扫一扫
微信扫一扫
 支付宝扫一扫
支付宝扫一扫
评论列表(0条)