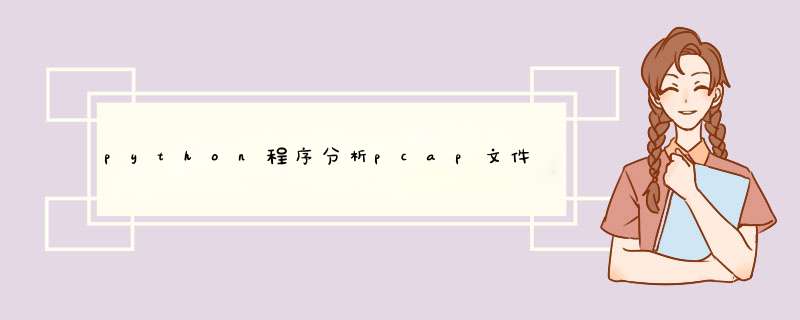
#!/usr/bin/env python
try:
import scapy.all as scapy
except ImportError:
import scapy
try:
# This import works from the project directory
import scapy_http.http
except ImportError:
# If you installed this package via pip, you just need to execute this
from scapy.layers import http
packets = scapy.rdpcap('f:\\abc123.pcap')
for p in packets:
print '=' * 78
[python] view plain copy
#print p.show()
for f in p.payload.fields_desc:
if f.name == 'src' or f.name == 'dst':
ct = scapy.conf.color_theme
vcol = ct.field_value
fvalue = p.payload.getfieldval(f.name)
reprval = f.i2repr(p.payload,fvalue)
print "%s : %s" % (f.name, reprval)
for f in p.payload.payload.fields_desc:
if f.name == 'load':
ct = scapy.conf.color_theme
vcol = ct.field_value
fvalue = p.payload.getfieldval(f.name)
reprval = f.i2repr(p.payload,fvalue)
print "%s : %s" % (f.name, reprval)
其中,p为数据包,scapy_http将其分为:
Ethernet->TCP->RAW三个层次,
使用p.show()函数可以打印出如下结果:
###[ Ethernet ]###
dst = 02:00:00:00:00:39
src = 00:00:00:01:02:09
type = 0x800
###[ IP ]###
version = 4L
ihl = 5L
tos = 0x0
len = 1014
id= 7180
flags =
frag = 0L
ttl = 45
proto = tcp
chksum= 0xbbf9
src = 126.209.59.13
dst = 121.113.176.25
\options \
###[ Raw ]###
load = '.....'
第一层是网络层,包含源、目的mac、ip协议号,第二层是tcp层,第三层包含端口号、http报文
其中每一层均为上一层的payload成员
字段显示的都是十六进制,其中的数据部分和wireshark打开,显示的十六进制窗口一样。
其实如果程序想到得到某一个或某几个字节的十进制数,用struct还是很容易转换的!
1、安装python-libpcap模块:使用pip安装:
pip install python-libpcap
2、使用python-libpcap模块读取pcap数据:
import pcap
# 创建一个pcap对象
pc = pcap.pcap('eth0')
# 设置捕获的数据包的大小
pc.setfilter('tcp port 80')
# 开始捕获数据
for ts, pkt in pc:
print ts, `pkt`
欢迎分享,转载请注明来源:内存溢出

 微信扫一扫
微信扫一扫
 支付宝扫一扫
支付宝扫一扫
评论列表(0条)