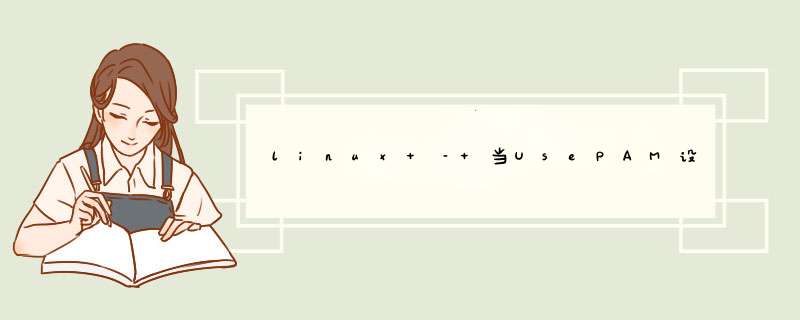
ChallengeResponseAuthentication noPasswordAuthentication noUsePAM no
当我尝试使用我的私钥登录时,我得到了
Permission denIEd (publickey).
如果我然后将UsePAM更改为是,我可以使用我的私钥登录.为什么?
我正在从OSX连接到Ubuntu 12.04 64位主机
ssh -i ~/.ssh/deploy -l deploy localhost -p 2222 -v
这是详细的ssh输出:
OpenSSH_5.9p1,OpenSSL 0.9.8r 8 Feb 2011deBUG1: Reading configuration data /Users/<user>/.ssh/configdeBUG1: Reading configuration data /etc/ssh_configdeBUG1: /etc/ssh_config line 20: Applying options for *deBUG1: Connecting to localhost [127.0.0.1] port 2222.deBUG1: Connection established.deBUG1: IDentity file /Users/<user>/.ssh/deploy type 1deBUG1: IDentity file /Users/<user>/.ssh/deploy-cert type -1deBUG1: Remote protocol version 2.0,remote software version OpenSSH_5.9p1 Debian-5ubuntu1deBUG1: match: OpenSSH_5.9p1 Debian-5ubuntu1 pat OpenSSH*deBUG1: Enabling compatibility mode for protocol 2.0deBUG1: Local version string SSH-2.0-OpenSSH_5.9deBUG1: SSH2_MSG_KEXINIT sentdeBUG1: SSH2_MSG_KEXINIT receiveddeBUG1: kex: server->clIEnt aes128-ctr hmac-md5 nonedeBUG1: kex: clIEnt->server aes128-ctr hmac-md5 nonedeBUG1: SSH2_MSG_KEX_DH_GEX_REQUEST(1024<1024<8192) sentdeBUG1: expecting SSH2_MSG_KEX_DH_GEX_GROUPdeBUG1: SSH2_MSG_KEX_DH_GEX_INIT sentdeBUG1: expecting SSH2_MSG_KEX_DH_GEX_REPLYdeBUG1: Server host key: RSA 50:db:75:ba:11:2f:43:c9:ab:14:40:6d:7f:a1:ee:e3deBUG1: Host '[localhost]:2222' is kNown and matches the RSA host key.deBUG1: Found key in /Users/<user>/.ssh/kNown_hosts:2deBUG1: ssh_rsa_verify: signature correctdeBUG1: SSH2_MSG_NEWKEYS sentdeBUG1: expecting SSH2_MSG_NEWKEYSdeBUG1: SSH2_MSG_NEWKEYS receiveddeBUG1: Roaming not allowed by serverdeBUG1: SSH2_MSG_SERVICE_REQUEST sentdeBUG1: SSH2_MSG_SERVICE_ACCEPT receiveddeBUG1: Authentications that can continue: publickeydeBUG1: Next authentication method: publickeydeBUG1: Offering RSA public key: /Users/<user>/.ssh/key1deBUG1: Authentications that can continue: publickeydeBUG1: Offering RSA public key: /Users/<user>/.ssh/deploydeBUG1: Authentications that can continue: publickeydeBUG1: No more authentication methods to try.Permission denIEd (publickey).解决方法 如果没有PAM(可插入的身份验证模块),则需要更复杂的ssh配置进行身份验证.你正在寻找这个,实际上:
# grep Password /etc/ssh/sshd_config PermitEmptyPasswords noPasswordAuthentication no
这将禁用passworded登录.确保正确建立公钥设置.
总结以上是内存溢出为你收集整理的linux – 当UsePAM设置为“no”时,SSH公钥验证失败全部内容,希望文章能够帮你解决linux – 当UsePAM设置为“no”时,SSH公钥验证失败所遇到的程序开发问题。
如果觉得内存溢出网站内容还不错,欢迎将内存溢出网站推荐给程序员好友。
欢迎分享,转载请注明来源:内存溢出

 微信扫一扫
微信扫一扫
 支付宝扫一扫
支付宝扫一扫
评论列表(0条)