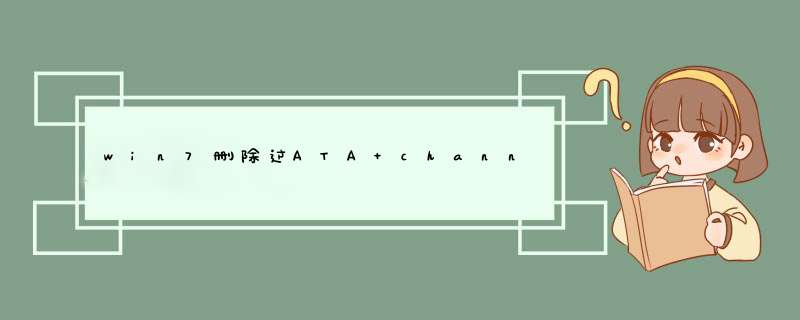
1、开机按F2进入BIOS,在Configuration------SATA Mode Selection这里按回车键选IDE,按F10再按回车。
2、或者是开机按f2进入BIOS设置,configuration项下有sata controller mode选项,选compatible为兼容(ide)模式,选ahci为sata模式,这里我们选择为compatible模式,然后按f10再按回车键退出。
我怀疑是系统的问题, 怀疑是一些垃圾文件, 注册表文件垃圾文件过多,没卸载干净造成的进安全模式去 *** 作
你可以用一些小方法试一下, ····试试 如果还不行 那就重装系统吧,
1、开始-运行-输入msconfig- 上面有个··启动,勾全部禁用然后·重启(这是开机启动项)
2、开始-运行-输入msconfig- 服务,看看里面是否有“未知”的服务,有的话 也是禁用
前两个呢是 关掉开机没用的进程, 保证开机速度能够正常, 或者是说有所提高。
3、用360安全卫士清理垃圾、清理插件、杀除木马,最后在杀杀毒 就OK了
遇到这个问题的人不少,Windows7下面的那个安全删除硬件下面一大堆的ATA Channel X,基本上发帖问的都是有强迫症的,也没人放Google找就发帖问,作为严重强迫症用户找到了解决方案,VMware官方文档。如果你是轻度强迫症用户,只需要按照官方文档说的,编辑VMX配置文件加上一句话就可以了
devices.hotplug = "false"
如果重度强迫症用户,连硬盘都不想看见,就按照这个解决方案,开机用脚本改注册表伺候。
MAKING AN EJECTABLE DEVICE UN-EJECTABLE
The way to get rid of the option to eject the virtual disk is to make Windows believe that it is not hot-pluggable. This can be achieved by modifying the corresponding device capabilities registry value. That, however, is complicated by the facts that only SYSTEM has write access to the registry key and that Windows re-writes the correct value when booting – re-enabling HotPlug. The solution is to execute a computer startup script via Group Policy. Startup scripts are run in SYSTEM context, and since the script runs every time the system is booted we can be sure the device capabilities value is always configured the way we want it to be.
To implement the solution, create a batch file with the following content and run it as a computer startup script:
Shell
1 :: Disable eject hard disk
2 :: Original value: 6
3 reg.exe add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\PCI\VEN_1000&DEV_0054&SUBSYS_197615AD&REV_01\4&1f16fef7&0&00A8" /v Capabilities /t REG_DWORD /d 2 /f
Note: The second command is for disabling network card ejection. This is an alternative to setting “devices.hotplug=false” in the VMX file.
Shell
1 :: Disable eject network card
2 :: Original value: 6
3 reg.exe add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\PCI\VEN_8086&DEV_100F&SUBSYS_075015AD&REV_01\4&3ad87e0a&0&0088" /v Capabilities /t REG_DWORD /d 2 /f
欢迎分享,转载请注明来源:内存溢出

 微信扫一扫
微信扫一扫
 支付宝扫一扫
支付宝扫一扫
评论列表(0条)