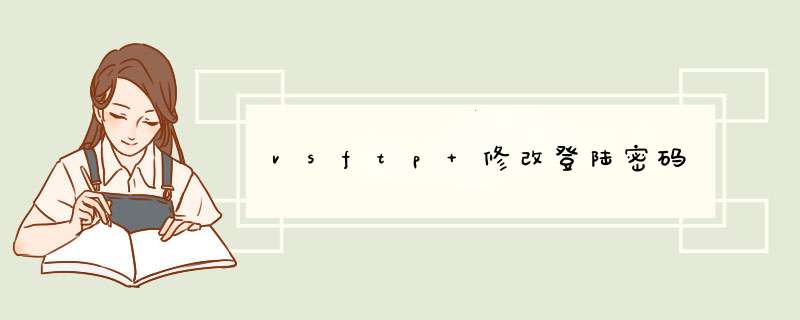
[root@localhost .ssh]# ssh-keygen –t rsa
Generating public/private rsa key pair.
Enter file in which to save the key (/root/.ssh/id_rsa):
Enter passphrase (empty for no passphrase): 按enter
Enter same passphrase again: 按enter
Your identification has been saved in /root/.ssh/id_rsa.
Your public key has been saved in /root/.ssh/id_rsa.pub.
The key fingerprint is:
e8:8a:5e:ae:c7:13:45:d0:81:cd:3f:e6:1e:f8:88:5a
root@localhost.localdomain
2.然后将Private Key 放在client上的宿主目录,一般放在/root/.ssh/目录中
并修改权限为user可读
3 最后,将Public Key 放在任何一个您想登陆主机server中的某user的宿主目录
下的.ssh/子目录人证文档中即可。
4现在192.168.0.6是client 想连接到192.168.0.8上用ssh-keygen –t rsa产生key
(-t参数是使用和种密码)这时在我的/root/.ssh/里边产生了三个文档分别是公钥
(id_rsa.pub)和私钥(id_rsa)另外要注意的就是id_rsa文档权限他必须是-rw------否则回不安全,id_rsa.pub就是公钥,把这个放到server目录上去用命令
[wds@localhost .ssh]# sftp id_rsa.pub
root@192.168.0.8
[wds@localhost .ssh]# passwd
[wds@localhost .ssh]# put id_rsa.pub
[root@localhost .ssh]# uploading id_rsa.pub to /root/.ssh/
[root@localhost .ssh]# exit
然后到服务器上去192.168.0.8
[root@localhost .ssh]# ssh –l root 192.168.0.8
[root@localhost .ssh]# cd /root/.ssh/
[root@localhost .ssh]#more id_rsa.pub >>authorized_keys 这样就能够了
[root@localhost .ssh]#
返回client上192.168.0.6
[root@localhost .ssh]# exit
[root@localhost .ssh]# ssh 192.168.0.8
比如你要实现不允许匿名用户登陆服务器:#vi /etc/vsftpd/vsftpd.conf
找到这句:
anonymouns=yes
把yes改成no,保存退出,
/etc/rc.d/init.d/vsftpd restart
就行了
同样:
#chroot_list_enable=yes
#(default follwer)
#chroot_list_enable=/etc/vsftpd.chroot_list
改成:
chroot_list_enable=yes
#(default follwer)
chroot_list_enable=/etc/vsftpd/chroot_list
保存后重新启动服务器:
/etc/rc.d/init.d/vsftpd restart
vi /etc/vsftpd/chroot_list
加入要做限制的用户就行了,以上三句可能记得不对,你可以去看看vsftpd.conf文件
欢迎分享,转载请注明来源:内存溢出

 微信扫一扫
微信扫一扫
 支付宝扫一扫
支付宝扫一扫
评论列表(0条)